Introduction
Emulation hacking is a sort of cybercrime that includes manipulating or abusing emulators, which are computer programs that let users run applications or video games on hardware that is different from their original hardware. Emulation hacking can be used for several things, including running homebrew programs and games and getting around copy protection in commercial games. Emulation hacking will be discussed in this article along with some of the ethical issues that surround it.
What is emulation hacking?
Emulation hacking entails changing or taking use of emulators to accomplish certain objectives. Emulators are software applications that simulate hardware behavior, enabling users to run applications or play games on hardware that is different from their original hardware. For instance, homebrew games and software that were never officially launched on a particular system can be run on contemporary hardware using emulators.
Emulation hacking takes this idea a step further by altering the emulator itself or taking use of flaws in the emulator to accomplish specific objectives. Emulation hackers, for instance, might change the emulator to allow games to run at a higher resolution or to get rid of copy protection features that bar gameplay without a valid license. ROM hacks, which are customized copies of already-released games that have been altered in a variety of ways, such as by adding new levels or characters, can also be made through emulator hacking.
How does emulation hacking work?
Several methods can be used to hack into emulation, depending on the hacker’s particular objectives. Modifying the emulator directly, either by making changes to its code directly or by developing “plugins” that change the emulator’s behavior, is a frequent strategy. With a hacker-created plugin, for instance, a commercial game’s copy protection might be removed, enabling play without a legal license.
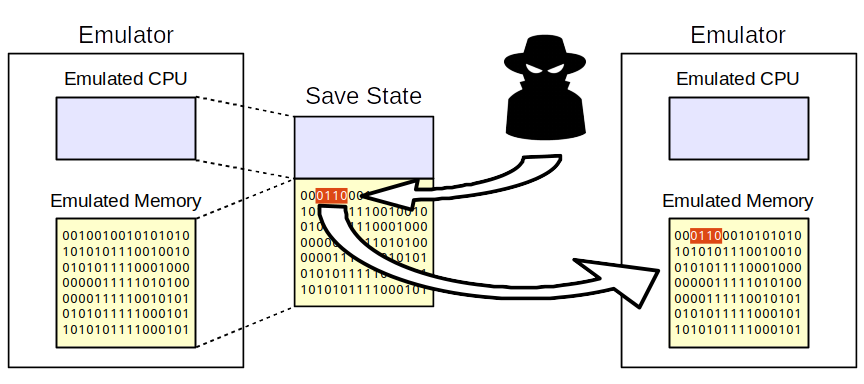
Exploiting flaws in the emulator or the software it uses is another strategy. For instance, some emulators include flaws that let hackers run code on the hardware below or get beyond security safeguards that bar unauthorized access. Hackers can execute their code or change the emulator’s functionality by taking advantage of these vulnerabilities.
Key Features of Emulation Hacking
The key aspects of emulation hacking include:
- Emulators: Emulation hacking involves using emulators, which are software programs that mimic the behavior of hardware, to run programs or games on platforms other than their original hardware.
- Modification: Emulation hacking often involves modifying emulators or creating plugins that alter their behavior, such as removing copy protection measures or running games at higher resolutions.
- Exploiting vulnerabilities: Emulation hacking can also involve exploiting vulnerabilities in emulators or the software they run, such as running code on underlying hardware or bypassing security measures.
- Preservation: Emulation hacking can be used to preserve and promote video game culture by allowing people to play games from older consoles that are no longer in production.
- New creations: Emulation hacking can also be used to create new games and applications that wouldn’t be possible on the original hardware.
- Ethical considerations: The ethics of emulation hacking are a subject of debate, as it can be used for both positive and negative purposes, such as distributing copyrighted content without permission. As with any form of hacking, it is important to consider the ethical implications of emulation hacking and to use it responsibly and legally.
Is emulation hacking ethical?
Emulation hacking’s morality is up for discussion. Emulation hacking, on the other hand, can be used to promote and preserve video game culture by enabling people to play games on vintage platforms that are no longer manufactured. Also, new games and programs that couldn’t be made on the original hardware can be made through emulator hacking.
Emulation hacking, on the other hand, can be used to get around copy protection systems and illegally and unethically disseminate content that is protected by copyrights. Emulation hacking can also be used to produce and disseminate ROM hacks that violate the publishers’ and developers’ intellectual property rights.
Advantages and Disadvantages of Emulation Hacking
Advantages:
- Preservation of video game culture: Emulation hacking can be used to preserve video game culture by allowing people to play games from older consoles that are no longer in production. This can help to keep classic games alive for future generations to enjoy.
- New creations: Emulation hacking can be used to create new games and applications that wouldn’t be possible on the original hardware. This can lead to a wealth of new content and ideas.
- Accessibility: Emulation hacking can make games and applications accessible to people who might not have had access to them otherwise. For example, people who live in countries where certain consoles were not sold can now play games from those consoles.
- Cost-effective: Emulators and ROMs can be cheaper than buying old consoles and games. This can make gaming more accessible to people on a budget.
Disadvantages:
- Illegal activity: Emulation hacking can involve distributing copyrighted content without permission, which is illegal and unethical.
- Technical issues: Emulators can be buggy and unstable, leading to technical issues and crashes. This can be frustrating for users.
- Ethical considerations: As mentioned before, the ethics of emulation hacking are a subject of debate. It is important to consider the ethical implications of emulation hacking and to use it responsibly and legally.
- Compatibility issues: Emulators may not be compatible with all games or software, leading to issues with running certain games or applications.
- Lack of original experience: Emulating games on different hardware can change the experience of playing the game, such as the feel of the controller or the graphical quality.
Final Thoughts
In conclusion, emulation hacking is a complex and controversial topic that raises many ethical and legal considerations. While emulation hacking can be used for positive purposes, such as preserving video game culture and creating new games and applications, it can also be used for illegal and unethical purposes, such as distributing copyrighted content without permission. As with any form of hacking, it is important to consider the ethical implications of emulation hacking and to use it responsibly and legally.

