In today’s digital age, computer security is of utmost importance. With the increasing reliance on technology for everyday tasks, the protection of sensitive data has become a critical concern for individuals, businesses, and governments alike. The consequences of a data breach can be devastating, ranging from financial loss to reputational damage and even legal repercussions.
What is Data Breach?
A data breach occurs when unauthorized individuals gain access to sensitive information. This can happen through a variety of means, including hacking, phishing, malware, and social engineering tactics. Once attackers have gained access, they can use the information for a variety of malicious purposes, such as identity theft, fraud, or espionage.
What causes Data breaches?
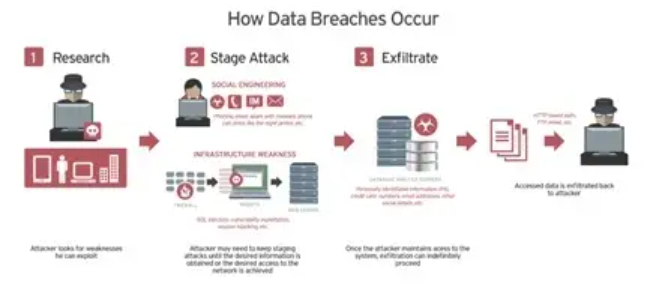
Data breaches can be caused by a variety of factors, including:
- Human error: This can include things like accidental disclosure of sensitive information, lost or stolen devices containing sensitive data, or simple mistakes like misconfigured security settings.
- Malware and hacking: Cybercriminals use various tactics to exploit vulnerabilities in software or networks, gain unauthorized access to systems, and steal data.
- Insider threats: These are threats posed by employees, contractors, or partners who have access to sensitive data and may intentionally or unintentionally misuse it.
- Physical theft: Physical theft of equipment, such as laptops or hard drives, can also lead to data breaches.
- Social engineering: Cybercriminals can use tactics such as phishing, pretexting, or baiting to trick people into giving away sensitive information or access credentials.
What are the 3 elements of Data breach?
The three elements of a data breach are:
- Confidentiality: Confidentiality refers to the protection of sensitive information from unauthorized access or disclosure. In a data breach, confidentiality is compromised when sensitive data is accessed or disclosed without authorization.
- Integrity: Integrity refers to the accuracy and completeness of data. In a data breach, integrity can be compromised if data is tampered with, altered, or deleted without authorization.
- Availability: Availability refers to the accessibility of data when it is needed. In a data breach, availability can be compromised if data is unavailable due to a cyberattack or other security incident.
These three elements are often referred to as the CIA triad, and they are essential to maintaining the security of data. When a data breach occurs, one or more of these elements is compromised, and sensitive information may be at risk. Organizations must take steps to protect the confidentiality, integrity, and availability of their data to minimize the risk of a data breach.
How to prevent Data breaches?
To prevent data breaches, it is important to implement robust computer security measures. This involves a multi-layered approach that includes hardware, software, and procedural safeguards. Some basic security measures include using strong passwords, regularly updating software, and using antivirus and antimalware programs. It is also important to encrypt sensitive data and use firewalls to prevent unauthorized access.
Organizations that handle sensitive information need to have a comprehensive security strategy in place to protect against data breaches. This includes implementing policies and procedures that ensure the safe handling of data, as well as training employees to recognize and report suspicious activity. Additionally, organizations should conduct regular security audits to identify vulnerabilities and implement necessary fixes.
In the event of a data breach, it is important to respond quickly and effectively to minimize the damage. This includes notifying affected individuals, securing the compromised systems, and conducting a thorough investigation to identify the cause of the breach. It is also important to be transparent about the breach and communicate with stakeholders to maintain trust and credibility.
Conclusion:
In conclusion, computer security is a critical concern in today’s digital age. Data breaches can have severe consequences, but by implementing robust security measures, organizations can minimize the risk of attacks. By staying vigilant and taking a proactive approach to security, we can all play a role in protecting sensitive information and ensuring a safer digital future.

